Preface
All the material below is part of a more general study “The Theory of the Structure of Hidden Systems”. This work is completely in the public domain and you can view it here here. Based on this theory, client-secure applications and anonymous networks are also being developed. You can find out about them Here.
In this article I did not leave links to literature. Such a list can be found in the main work “The Theory of the Structure of Hidden Systems”, because this article is only an integral part.
Introduction
Anonymity is a complex term that incorporates many factors that ultimately influence, to one degree or another, the level of anonymity itself. Due to this, anonymity can always be interpreted differently, depending on situations, and you can always remain correct in your judgments. The purpose of this article will be the destructuring of such anonymity specifically in the network space, because outside this space the term itself takes on an even more abstract, general character..
This article may be useful to developers designing anonymous networks, or cryptographers working on cryptographic protocols and directly related to the analysis of anonymous communications between multiple entities. Also, this work may be useful simply to people who are interested in the component of anonymous networks.
Network anonymity expresses itself directly in hidden (anonymous) networks. Today there are quite a large number of such networks, and fortunately they are heterogeneous in their content, due to which their subsequent comparisons become possible, as well as the analysis of anonymity itself due to their differentiations.
You can start any analysis either from the very beginning (from sources and primitives) or from the end (from already existing systems). Either of these two analyzes will ultimately (if done correctly) lead to the same truth. However, back-to-back analysis is more problematic if no underlying data is available. Such initial data can be obtained by destructuring ready-made systems and expressing the resulting forms as the beginning of research.
Anonymous networks
Hidden systems are a variety of network technologies aimed at ensuring and maintaining an acceptable level of anonymity of end subjects (sender and recipient) in conjunction with the security of objects (information). At the same time, anonymity and security can be implemented to varying degrees, which makes the class of such systems quite extensive. Systems of this kind include anonymous networks and client-secure applications. In the context of this work, only anonymous networks will be analyzed.
Anonymous (hidden) networks are networks that connect and combine routing (distribution of an information object over a network) together with encryption (a method of hiding an information object on a network). Routing provides an anonymity criterion aimed at subjects, encryption provides criteria for confidentiality (primarily), integrity and authentication aimed at an object. Without routing, the sender/recipient can be easily determined; without encryption, the transmitted message can be easily determined. Thus, only in combination of these two properties can a network be hidden.
Based on the speed and method of information dissemination, there are two types of anonymous networks – with low and high latency. Systems with low latency place speed and efficiency in transporting information between its true subjects as a basic necessity, while the level of anonymity of such networks is insufficient to counter attacks from external global observers (as a factor of strong anonymity). Systems with high latency place a real level of anonymity as a basic necessity, including that aimed at counteracting global observers, but at the same time, transmission speed becomes the most important drawback in such networks. From the above, the classic problem of designing secure systems follows - the choice of compromise between performance and security. Examples of systems with low latency include Tor, I2P, Tarzan, etc., and with high latency - Mixminion, Herbivore, Dissent, etc..
Routing in anonymous networks is not primitive and puts the efficiency of object propagation into the background (including systems with low latency, otherwise they would not be hidden networks), because the main goal is to create an obfuscation algorithm (anonymizer) that would lead to the complexity of analyzing the true path from the point of departure to the point of destination. The productivity and efficiency of “pure” routing is lost, replaced by a feature of the algorithm. In such conditions, the hidden networks themselves become slow and difficult to use (including with low latency), which also partially or fully delays their applied and everyday use at the present time.
The tasks of this type of routing involve threat models that take into account the capabilities of attackers. The main antagonist in such conditions becomes the state, as an external, global observer, capable of viewing the distribution of objects across the network on a large scale. In this case, the routing algorithm must be able to confuse the external adversary and not provide the ability to identify patterns of sending, receiving, requests and responses by participants in the anonymous network. Other, and no less serious, opponents are internal attackers, when its participants themselves become a negation of the system, its decomposition. It is assumed that external observers, in addition to analyzing network traffic, are also able to block running nodes in the system, thereby considering their unique combinations and behavior patterns. Internal observers are able to fill the network with cooperative nodes and, in addition to routing, also perform additional actions, such as sending and receiving information. Observers without additional functions are called passive attackers, otherwise - active. In such realities, the routing algorithm must exclude literally every subject (sender, recipient and intermediate) from a full analysis of received and sent packets.
In their totality, in the synthesis and collusion of external and internal attackers, attacks are capable of manifesting themselves that would previously have been impossible individually. In abstraction, the main attack methods, as a set, can be depicted as Tables below. At the same time, from the definition of active attacks it turns out that they are a superset of passive ones, that is, A belongs to C And B belongs to D. Also, external attacks can be conditionally divided into two components, subsets: {B1,B2} And {D1, D2}, where is the set {B2,D2} is a representation of external attacks with a global observer, and {B1, D1} therefore without it = {B\B2, D\D2}.
| Internal attacks | External attacks |
Passive attacks | A | B |
Active attacks | C | D |
Anonymous networks can have different threat models depending on how they are used and their budgetary or technical constraints. Based on this, three types of anonymity are formed:
Anonymity of communication between sender and recipient. It represents a weak threat model, because it allows observers to record the facts of sending and receiving information by true subjects of the network. Such systems have low overhead and, as a result, can be used in a fairly wide variety of implementations. Examples of such networks are Tor, I2P, Mixminion.
Anonymity of the sender or recipient. This network has an average threat model, in the sense that it hides only the fact of sending or only the fact of receiving information by one of the subjects (either the sender or the recipient). Such systems can be well applied only in private implementations, as opposed to anonymity in relation to a second subject, where protection of the sender (for example, when accessing a hidden service through a botnet) or the recipient (for example, when accessing a service in the open Internet space) is not required).
An example of such networks could be a network where the sender transports a fully encrypted message to all participants in the network, which can only be decrypted by someone who has a private key specific to this message (if asymmetric cryptography is used here, of course). Theoretically, everyone can recognize the sender of information, but finding out the recipient and whether he even exists is extremely problematic, because in theory, anyone can be the recipient, because everyone gets these messages.
Another example could be a network where, over a certain period, information is generated by all network participants and sent to one server through several routers unrelated to each other by common goals and interests (that is, they are not in collusion). The receiving server decrypts all information and (as an example) publishes it in clear text, as a result of which all network participants receive information from many anonymous senders.
Anonymity of the sender and recipient. It represents an expression of a strong threat model, because it simultaneously hides both the fact of sending and the fact of receiving information. In other words, we assume that the recipient always needs to respond to the sender, in other words, a request-response model is created. In such a system, it becomes impossible to apply “anonymity of the sender or recipient”, because the sender will sooner or later become the recipient, and the recipient will become the sender, and therefore the threat model based on the second type will begin to regress and become a model based on the first type - “anonymity of the connection between the sender and the recipient.” Such systems, due to their computational difficulties and limitations, are often of little use in practice. An example of such networks is DC networks.
The first point refers to the unlinkability criterion, while the second and third points relate to the unobservability criterion. The unobservability criterion already includes the unlinkability criterion. If we go from the opposite and assume the falsity of this judgment (that is, the absence of unconnectability in unobservability), then it would be possible, using unconnectability, to determine the existence of subjects of information and, thereby, allow a violation of unobservability, which is a contradiction for the latter.
The third point is problematic in terms of description, because the condition becomes unknown - how anonymous the sender and the recipient are to each other, and whether non-anonymity to each other should be considered a violation of anonymity, especially if such connections are built on mutual de-anonymization to each other. One way or another, this question depends on the implementation and method of application of the final hidden network.
Hidden networks with theoretically provable anonymity are considered to be closed (fully eavesdropped) systems in which it becomes impossible to carry out any passive attacks (including the existence of a global observer) aimed at de-anonymizing the sender and recipient with minimal conditions regarding the number of nodes not subject to collusion. In other words, from the point of view of a passive attacker, a posteriori knowledge (obtained as a result of observations) should remain equal to a priori knowledge (before observations), thereby maintaining an equal probability of de-anonymization by N-many network subjects.
From the specific form of routing, criteria are identified on the basis of which it can be stated that the network is anonymous. For example, networks Tor, I2P, Mixminion, Herbivore, Crowds, etc. are anonymous networks because they ensure the anonymity of subjects due to the existence of obfuscated routing, and minimal security of objects in communications between initiators and communication platforms. Networks RetroShare, Freenet, Turtle, Bitmessage, etc. are not anonymous networks, because routing represents only the fact of transmission (to some extent and specific due to the hybrid or peer-to-peer nature of the network architecture), transporting information without the direct application of an obfuscating algorithm, although the systems themselves provide a high level of security for objects. Networks that provide exclusively the anonymity of subjects in isolation from the security of transmitted objects are also not hidden networks. Such an event is extremely specific, but is possible using the example of “pure” DC networks, as non-classical forms of the first stage of anonymity.
Development of anonymity
Because network anonymity is an object fragmented in terms of definitions and terminologies, we can assume heterogeneity and the fact of formation and development in certain stages. In short, it really becomes possible to interpret anonymity as a kind of gradation, phasing, which is characterized by six stages, revealing the process of its formation through phases of negations and internal contradictions.
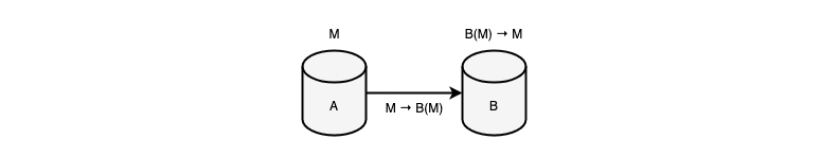
The first stage is the starting point of anonymity, a thesis, a monad that does not primitively represent anonymity, an emptiness that initializes the power of anonymity |A| = 0*. An example is the existence of only a direct, straightforward, primitive client-to-client connection between two peers, which amounts to a state of stasis. Due to the absence of intermediate subjects, the power of trust* at this stage represents the minimum possible value.

Figure 2. First stage of anonymity (direct connection) The second stage, becoming an antithesis, begins to deny the first stage, lead the system to primary metastasis, change with its own transformation the method of interaction between subjects, add to its shell a new role of an intermediate node, a server, subordinating all other subjects to private-personal service. Thus, the architecture becomes multi-peer, clients begin to depend on communication platforms, and the power of anonymity increases to a constant value. The stage provides (initializes) only client-client anonymity, but ignores client-server anonymity, which leads to static anonymity power |A| = 1. In other words, the server begins to have sufficient information about clients, clients, in turn, begin to communicate through the server, which leads them to actual differentiation, to mutual anonymity and dependence on a common platform. In this situation, it is worth noting that anonymity and security go against each other, they oppose each other, because on the one hand, the security of the “client-client” connection becomes compromised and discredited, and at the same time, on the other hand, its anonymity becomes the initializing and first simplest form of anonymity. This contradiction (deterioration of security and improvement of anonymity) is not accidental, but represents a rule and pattern, as can be seen later. The described stage is briefly called pseudo-anonymity, and clients - anonymous.

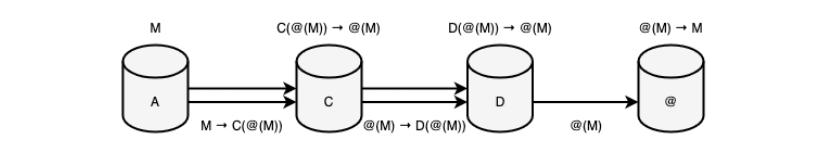
Figure 3. Second stage of anonymity (connection via service) The third stage, being a synthesis of the previous stages, represents primitive routing, and therefore primitive anonymity, of several proxy servers unrelated to each other. It is at this stage that the network becomes fragmented, uncertain, hybrid, due to which the power of anonymity increases by striving for a static value lim|A|→C, Where C — number of proxy servers. This method involves building a chain of nodes through which the packet will pass. The power of anonymity at this stage is indeed increasing, but the security of the subjects themselves is not yet ensured. This is all connected because encryption at this stage is an additional property (akin to the second stage), which does not provide protection for the client-client communication, and therefore does not lead to a decrease in the power of trust. On Pictures below depicts an abstract subject @, capable of being both a real recipient and an intermediate entity - a service.

Figure 4. Third stage of anonymity (Proxy broadcast) The fourth stage, as a development of the third stage, initiates the method of variability, multiple encryption, polymorphism of information* through its tunneling. This stage includes VPN services (virtual private networks) such as N-This combination of proxy servers with internal encryption layers, where the power of trust and the power of anonymity is equivalent to the third stage. A distinctive feature of the fourth stage is the existence of output nodes that gradually “reveal” the true packet created before the initial tunneling on the sending side, which makes it possible to hide the metadata connecting the message initiator and the destination server. In this regard, this stage changes the routing method, gives it the property of polymorphism as the variability of private information as it moves from one node to another, and removes intermediate nodes from analyzing and comparing encrypted information. This method hides the real connection between subjects through their object, and therefore the anonymity begins to acquire a more true character, in which the system’s desire to increase and contain the power of anonymity becomes better in comparison with the third stage.

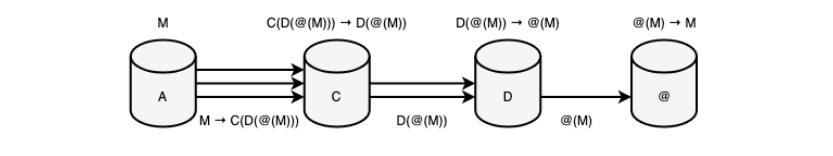
Figure 5. Fourth stage of anonymity (VPN tunneling)) The fifth stage, being a synthesis of the first stage and a negation of the third, becomes the point of final replacement of the network address with a cryptographic one, at which the identification of subjects is separated from the concept of network protocols, subordinating the nodes to an abstract cryptographic model. Network communication platforms are built as bases, on top of which cryptographic connections grow, encapsulating the interactions of subjects with their base. It is at this stage that the power of trust again becomes the minimum possible value, and therefore all applications built at the fifth stage of anonymity have a security level that depends only (or to a greater extent) on the quality of the client part itself. An example of such a stage can be chats, instant messengers (Bitmessage), email, forums (RetroShare), file services (Freenet, Filetopia), blockchain platforms (Bitcoin, Ethereum), etc., where cryptographic addresses become the main factor in identifying clients ( public keys, public key hashes). The network begins to represent not only a hybrid, but also a peer-to-peer behavior of nodes with a possible and additional dynamic way of determining the power of anonymity, as 0 < |A| <= N, Where N — the number of nodes in the network, determined by blind, flood routing and cryptographic identification. At the same time, it is worth noting that at this stage there is no any polymorphism of information (as was the case in the fourth stage), which leads to internal contradictions of simultaneous progress and regression of anonymity. Therefore, the fifth stage can be briefly characterized by ignoring anonymity (exotericism) on the part of the subject and preserving it (esotericism) in the transmitted object. On Picture below “network” means switching the system from the state of network identification to cryptographic identification, as a result of which information about the sender is abstracted for the recipient and about the recipient for the sender directly.

Figure 6. Fifth stage of anonymity (connection via abstract network) The sixth stage leads to a one-time negation and synthesis of the fourth stage, as a system not focused on anonymous identification of subjects, and the fifth stage, as a system not aimed at anonymous communication between subjects. This synergy combines the properties of polymorphism (anonymous binding) and cryptographic identification (anonymous determination), which leads not only to the anonymity of the sender of information, but also to the depersonalization of the recipient, as a result of which the definition of anonymity becomes more qualitative and complete. The power of anonymity at this stage becomes equivalent to the fourth stage, as well as the power of trust (the reason for the deterioration in the power of trust relative to the fifth stage is given in the subsection “Problems of security of anonymous networks”). An example of the sixth stage is most hidden networks, like Tor (onion routing), I2P (garlic routing), Mixminion (mix network), etc. On Picture below. shows a prototype of the functioning of the Tor system with a request oriented to an internal resource (as a simplification, a diagram with two intermediate nodes is shown).
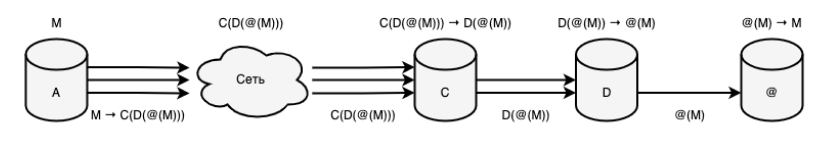
It is worth noting that the fourth and fifth stages appear parallel to each other, which leads to the difficulty (or rather even impossibility) of accurately recognizing and determining the sequence of development of anonymity as a whole. This order of stages was taken according to the number of qualitative changes. For example, in the fourth stage (relative to the third) only information polymorphism was added, while in the fifth stage the power of trust was reduced, cryptographic identification appeared, a new routing method emerged and support for peer-to-peer connections returned. On the other hand, the fifth stage could also rightly become the fourth, based not on the development of anonymity of subjects, but on the development of security of objects. In this case, the fifth stage would be the final form, while the current fourth stage would not be designed at all.
It is also worth noting that the second and fifth stages of anonymity are characterized by the implosive nature of information behavior to a greater extent than all other stages, because the first involve not only a method of distributing objects, but also the ability to contain them for subsequent extraction and consumption. Such stages are called communication platforms, because communication itself between subjects begins to be ensured not only by the continuous transportation of objects (as the very fact of transmission), but also by the “loading”, through intermediate subjects, of previously stored objects, the basis of which already contains information about the sender and/or recipient. Other stages abstract from the final consumer of information and focus only on the method of transmission itself. The only exception to all of the above is the first stage of anonymity, where the very fact of transmission is at the same time a way of finally receiving information.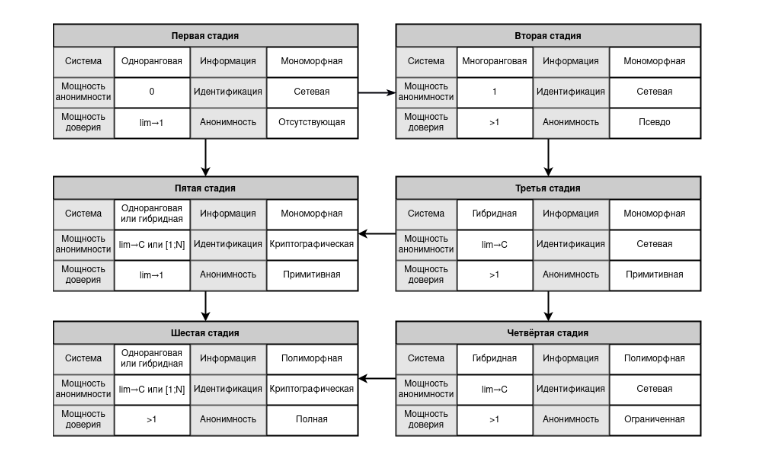
The protection defined by the client-client relationship begins at the first stage of anonymity and is subsequently immediately replaced by client-server encryption of the second stage. Such a rapid substitution and decomposition of direct communication into a communication platform is due to the inability and limitation of the first stage for explosion, expansion of network “borders”, in which subjects are not able to communicate en masse without creating intermediate nodes. The subsequent and higher-quality revival of secure “client-client” communication, which removes the limitation in expansion, appears at the fifth stage and ends exactly there, because the goal of all subsequent stages is already to hide the subjects of information through methods of transporting an object based on cryptographic addresses, where more the question of the truth of the receiving party is not raised.
The main advantage of the fifth stage of anonymity is the ability to identify subjects in peer-to-peer and hybrid systems based on cryptographic methods, which leads to integrity, as well as authentication of transmitted information, independent of third-party nodes and servers. Additionally, the property of confidentiality may appear, where information begins to represent the essence of a secret, secret, encrypted, rather than an open and shared object. But the confidentiality property itself at this stage is an additional criterion, and therefore can be removed if it is redundant for the system itself. As an example, cryptocurrencies have integrity and authentication properties, but not always confidentiality.
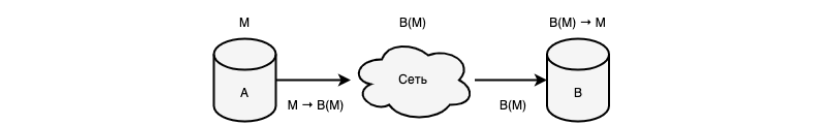
Based on the fifth stage of anonymity, it becomes possible to form secret communication channels of the first form as presented in Picture below. This property is achieved by the emergence of cryptographic identification of subjects, thanks to which it becomes possible to abstract from network identification.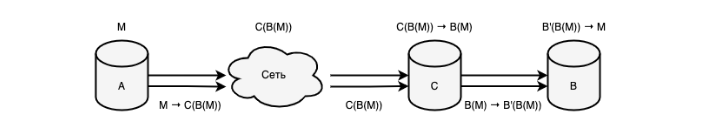
Based on certain subsets of the fifth and sixth stages of anonymity, it becomes possible to form secret communication channels of the second form.
Thus, secret communication channels in their general properties are abstracted from the primary network, but not by negating it, but by merging with it, due to which they build their own methods of communication and begin to be based on the fifth or sixth stage of anonymity.
From all of the above, we can deduce the main criteria (points) of anonymity on the basis of which the formation of anonymous networks with an increased level of security (complete hidden systems) will be available).
Anonymity must be internal, regarding analysis by nodes, and external, regarding analysis of network traffic. This criterion must be determined by the severance of communication between subjects through their object based on an obfuscating routing algorithm.
Anonymity is required to have encapsulated and abstracted aliases between sender and recipient to primary identification based on network communications. This criterion should be determined by the severance of the connection between network and cryptographic identification.
Anonymity is required to prevent data and metadata from being stored in a transparent state for intermediate nodes. This criterion should be conditioned by the replacement of all communication platforms with the fifth stage of anonymity, thereby reducing the power of trust to a theoretically possible minimum.
The second point is to a certain extent a simplification, because the disconnection should also occur between two cryptographic identifications of dissimilar systems merging into one whole system, and not just between network and cryptographic identifications. For example, if the fifth and sixth stages are combined with each other, then the cryptographic identification of the same subject should “split” into the fifth and sixth stages, respectively. Thus, in such a synthesis, the identification of a subject should be expressed as a sequence of identifications of the form “network → cryptographic (sixth stage) → cryptographic (fifth stage)».
A hidden system endowed with only the first two points is an anonymous network and belongs to either the first^, fifth^, or sixth stage of anonymity (the first^, second^ stages will be discussed further). A hidden system with only the last two points is a client-safe application and belongs exclusively to the fifth stage of anonymity. A hidden system equipped with three anonymity criteria at once is complete and belongs not to a separate stage of anonymity, but to their combinations. A system endowed with only one point out of three is not hidden. The system with the first point can be understood as VPN tunneling (the fourth stage of anonymity), and the second - communication services (the second stage of anonymity). There are no systems with only the third point, just as there are no combinations of the third point with the first (excluding the second). This is due to the fact that the third criterion is a consequence of the second (the reverse judgment is false). All of the above descriptions can be presented in a briefer description of examples.:
1. Built “chain” of VPN services ∈ first point;
2. Centralized communication services ∈ second point;
3. Anonymous networks = first point ⋂ second point;
4. Client-secure applications = second point ⋂ third point;
5. Complete hidden systems = first point ⋂ second point ⋂ third point;
Thus, based on the above criteria of duties of the type “to be, to have, to prevent”, it is possible to identify a basic definition of anonymity regarding the general type of hidden systems, where network anonymity will be understood as the breaking of most logical connections between a transported / stored object and its subjects, as well as between the network and cryptographic identification.
It is worth noting that this definition is still abstract, because does not indicate a specific and supported anonymity criterion by a particular hidden system. For example, according to this definition, the unknown variable is the level of anonymity of the sender and/or recipient in the hidden network, because the anonymization mechanisms and vectors themselves are unknown. In other words, the above designation does not define who or what exactly this system protects - the sender, the recipient, both of them, or just their connection. However, this same abstractness simultaneously brings clear boundaries in the definition of anonymity between heterogeneous systems. The power of anonymity is the number of nodes lined up in a chain and participating in routing information from the sender to the recipient, without being in any way connected by common goals and interests. It follows that the multi-peer architecture has the power of anonymity by default |A| = 1 (regardless of the number of servers). Zero anonymity power |A| = 0 occurs when there are direct connections between subjects (in other words, in the absence of any routing). So for example, if R = {A, B, C} — is the set of nodes participating in routing, and a subset{A, B} belongs R — cooperating nodes, then Q(R) = [{A, B}, {C}] and as a consequence, |A| = |Q(R)| = 2. The term power of anonymity |A| taken as a corollary of the anonymity set term A, implying R-the number of subjects capable of performing actions in the system for a single transaction. Unlike the anonymity set, the power of anonymity imposes an additional restriction in which colluding nodes are considered to be one node Trust power is the number of nodes participating in the storage or transmission of information presented in the open description. In other words, such nodes are able to read, replace and modify information, because for them it is in an extremely pure, transparent, transparent state. The greater the power of trust, the higher the expected chance of compromising individual nodes, and therefore the information stored on them. It is considered to be one of the recipient nodes. So zero trust power |T| = 0 will arise only in moments of absence of any connections and connections. If |T| = 1, this indicates that the communication is secure, in other words, no one except the sender and recipient owns the information. In all other cases |T| > 1, which indicates a group connection (that is, the existence of several recipients), or intermediate nodes capable of reading information in clear text. Information polymorphism is the property of variability of a transmitted object during multiple routing by several network subjects, delimiting the connection of subjects through analysis of the object. So for example, if there are three network entities {A, B, C} and object P, which is transmitted from A To B and from B To C accordingly, the appearance of the information P1 And P2 should be defined as [P1 = (A → B)] ≠ [P2 = (B → C)], Where P ∉ {P1, P2}, B doesn't connect {P1, P2} WITH P And (A doesn't connect {P1, P} WITH P2 and/or C doesn't connect {P2, P} WITH P1). In most cases, information polymorphism is achieved by multiple object encryption: [e2(e1(P)) = (A → B)] ≠ [e1(P) = (B → C)], in which the interstitial subject B becomes impossible to bind {e2(e1(P)), e1(P)} WITH P, and subject C is unable to bind {e1(P), P} WITH e2(e1(P)).Details
The power of anonymity

Details
The power of trust
Details
Information polymorphism
First stage of anonymity
When initially considering the first stage of anonymity, the simplest form is expressed, initializing the development of the anonymity, in which the straightforwardness of the connections creates the primitiveness of its organization. But with further and more detailed analysis of anonymous networks, one can notice an exceptionally contradictory property of the first stage of anonymity, which at first excludes, and upon revision forms theoretically absolute anonymity in the inherent straightforwardness of the subjects. This quality arises when generating an object capable of hiding all information about the subject, including the very fact of its transmission and storage. In such a system there is no actual routing (which eliminates all stages above the first). Based on this quality, two paradoxes emerge.
The first stage of anonymity excludes intermediate subjects from its consideration. If this stage passes into the state of an anonymous network, then communication services based on either the second or fifth stages of anonymity can emerge within it. Thus, the recipient in the anonymous network becomes unequal to the final recipient, which contradicts the definition of the first stage of anonymity.
The power of trust in the first stage of anonymity has the minimum possible value. If this stage passes into the state of an anonymous network, then communication services based on the second stage of anonymity can emerge within it. Thus, intermediate nodes appear that play the role of final recipients, which leads to an increase in the power of trust and, as a result, contradicts the definition of the first stage of anonymity.
All paradoxes are based on the most dual form of the first stage, when it simultaneously absorbs both the expressed transportation of the object and its final storage. Paradoxes, by their existence, actually split duality and form a new subset, as an implicit gradation of the first stage of anonymity. In all subsequent references, the above-described stage with its inherent paradoxes will be displayed as the “first stage of anonymity”, with a circumflex sign. As an example of the existence of the first stage of anonymity, hidden networks based on the problem of dining cryptographers (DC networks), such as Dissent and Herbivore, are highlighted. The pure form of the first stage of anonymity leads to the following disadvantages:.
Scalability. The first stage of anonymity leads to the need to build a large number of direct connections, which leads to a scalability problem, where each new user is required to connect to all existing network participants. The problem is solved by transferring the first stage of anonymity to higher order gradations, forming intermediate nodes that do not completely affect the level of anonymity in the network. Dissent moves the system to the third stage of anonymity, Herbivore to the third with a local topology and to the fifth with a global topology.
Collisions. There can only be one message sender at a time. When messages are generated in parallel by two or more network participants, a collision occurs, leading to overlap of information. In most studies, the problem is solved by setting a message generation schedule, which leads to a mandatory sequence. For schemes of this kind, Dissent uses shuffles, and Herbivore uses small groups.
Pure anonymity. In its original form, the anonymity of the first stage is completely separate from the security of the transmitted object, where the dissemination of information occurs only on the basis of a broadcast connection, in which the entire system is the recipient of the message. To ensure a secure line of communication from the sender to a single recipient (true or intermediate), there must be a transition from the first stage of anonymity to the fifth gradation in the concept of a secret communication channel.
However, pure anonymity only limits the application of the first stage of anonymity, through the anonymization of the only party - the sender, but does not in any way contradict the definition of anonymity of hidden networks.
Thus, the first stage of anonymity, as a pure form of expression of the anonymous person, is difficult to apply in modern realities due to critical shortcomings, which leads to the need to combine this stage with higher-order gradations. It is also possible to identify an interesting pattern that divides the first stage of anonymity into two vectors of development - provable security of objects without anonymity of subjects (classical first stage) and provable anonymity of subjects without security of objects (first stage with paradoxes or non-classical form) for non-broadcast connections.
The first vector is based on the security of objects, as a result of which subsequent polymorphism of information becomes possible as a method for constructing obfuscating routing. The second vector is based on the anonymity of subjects, as a result of which it becomes necessary to combine it with a secret communication channel, as a method aimed at ensuring the security of objects. Both vectors ultimately converge at the point of subject anonymity with an acceptable level of object security based on cryptographic identification, as depicted in Picture below.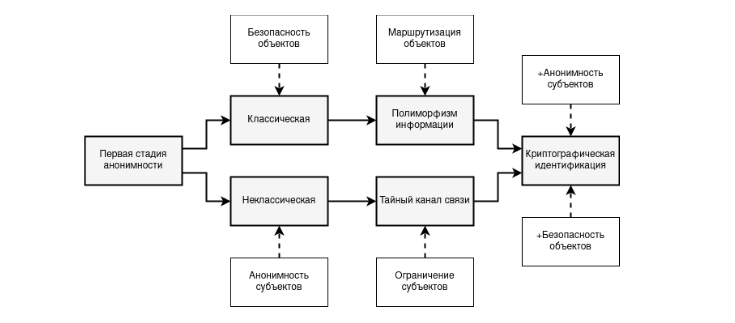
At the end of this section, it is worth noting one important component. The first stage of anonymity, which at first appears to have no routing, clearly begins to contradict the term “anonymous network.” Nevertheless, routing, although specific, exists in the first stage. This can be proven by the fact that participants in such a network cooperate and combine information into one output bit sequence, where even when communicating «all-to-all» already “crossed” information is transmitted. This method of routing cannot be explicitly called polymorphism, although there are certain similarities, because the information itself is not distributed by the system, but is generated by it from within.
Fifth stage of anonymity
By the definition of the first stage of anonymity, it can be assumed that if the fifth stage of anonymity has confusing routing other than information polymorphism, then it will no longer be the fifth stage due to its inconsistency.
And indeed, if an anonymous network is formed on the basis of the fifth stage of anonymity, where polymorphism of information ceases to exist, then such a system will have to incorporate the main criterion of hidden networks, namely the ability to create communication services.
Communication services built in an anonymous network can be based on the second stage, which leads to an increase |T| power of trust. This, in turn, contradicts the fifth stage of anonymity due to belonging to services with theoretically minimal trust power. This paradox is based on the specifics of an obfuscation algorithm that does not belong to the polymorphic routing class. Thus, this stage cannot be fully considered the fifth stage of anonymity (by the nature of its broadcasting of information, and not storage as a communication service) and the sixth gradation (due to the lack of polymorphism of information). For this reason, and quite correctly, this stage can be considered the fifth stage of anonymity, as was identified and done earlier with the first stage of anonymity.
Constructs of anonymity
Anonymous networks are based on certain patterns, constructs or design primitives, which take into account the roles of subjects and constructed threat models. In the simplest cases, only one design pattern is used, in others combinations of similar patterns are used, which can lead to some improvements, new features and, in parallel, to the complication of the final application logic.
One and the same design pattern may have different, variable mechanisms of its execution - properties. A distinctive feature of many properties from each other is the mechanism for issuing final information based on the input received sequence. These properties have qualities that allow them, depending on the task, to provide a certain level of anonymity, performance and applicability. Three main properties can be distinguished.
«Threading." If the algorithm receives correct (valid) information as input, then the necessary action, such as a response, must be performed immediately after processing the input sequence. Represents the best quality of computational performance (compared to other properties) at the expense of reducing the quality of anonymity. In terms of methods of application, it is a leading property. As an example, the Tor network and onion routing.
«Periodicity". If the algorithm receives correct (valid) information as input, then the necessary action, as a response, should be performed only after a period equal to T dependent or independent of the time of received information. May represent the best quality of anonymity (compared to other properties) at the cost of reducing the quality of computational performance. Has the smallest number of uses due to its overhead. As an example, the Herbivore network and a set generation schedule.
«Accumulativeness." If the algorithm receives correct (valid) information as input, then the necessary action, such as a response, should be performed only after acceptance N-a lot of other information. Represents good anonymity qualities at the cost of reducing the quality of computational performance. Has a limited number of uses. As an example, the Mixminion network and the Mix networks architecture).
Anonymous network design patterns (hereinafter referred to as constructs) represent specific communication between several subjects, depicted in the form of graphs. Due to the method of communication between nodes and the selected properties, such a construct determines further and possible ways of using the constructed scheme. Three main constructs can be distinguished.
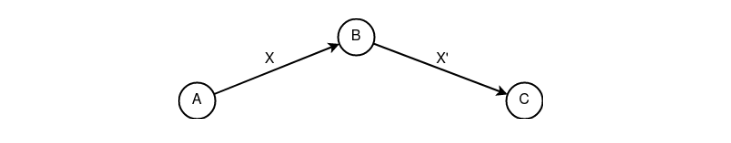
«Following." A basic construct that represents polymorphism of information in its simplest form. Often used in its pure form by anonymous networks due to the ease of formation of the properties of non-connectivity between subjects of information.

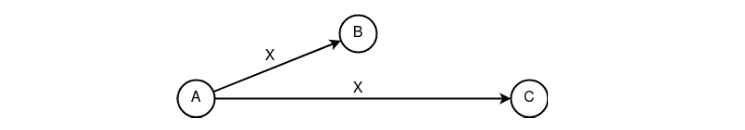
Figure 11. Basic construct “following”» «Spreading". A basic construct that represents in its pure form the ability to strongly abstract network and cryptographic identification from each other. Using the “periodicity” property can lead to concealment of the fact of sending and/or receiving information.

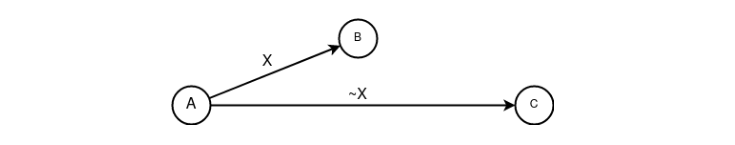
Figure 12. Basic construct “diffusion”» «Entanglement." A basic construct that represents in its pure form the falsity of the fact of sending information. It is impossible to apply in its pure form due to the lack of the very fact of transmitting information. Serves exclusively as a composite part for composite structures.

Figure 13. Basic construct “entanglement”»
Based on the basic constructs, it is possible to form composite constructs that lead to certain improvements. A composite construct can be represented by a combination of the same underlying construct only if it is applied inconsistently. Multiple composite constructs can have the following representations.
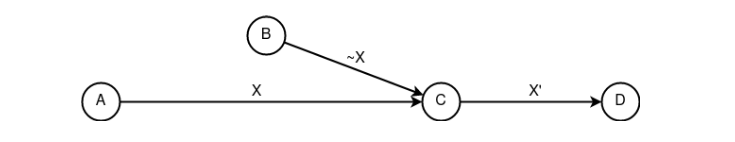
«Mixing". A composite construct that is a summation of the “following” constructs. Allows you to improve the criterion of unconnectability of subjects through the uncertainty of the state of the object. Often used implicitly when using the "threading" property».

Figure 14. Composite construct “mixing”» «Split". A composite construct that is a combination of the basic constructs “diffusion” and “entanglement”. Allows you to improve the criterion of unlinkability of subjects by generating false messages.

Figure 15. Composite construct “splitting”» «Mixing." A composite construct that is a combination of the basic constructs “entanglement” and “following.” In essence, it is the opposite action to “splitting”».

Figure 16. Composite construct “reduction”»
As a result of all of the above, as an example, it becomes possible to build network communications with the anonymity of the connection between the sender and the recipient, the anonymity of the sender or recipient, the anonymity of the sender and the recipient. Each example presented also theoretically becomes another variation of a composite construct.
An example of network communication with anonymity of communication between the sender and the recipient based on the constructs of “following” and “mixing”. Representatives of this type of communication can be considered networks Tor, I2P, Mixminion (the difference between the latter network and similar ones lies only in the predominant use of the “accumulative” property over the “threading” property»).

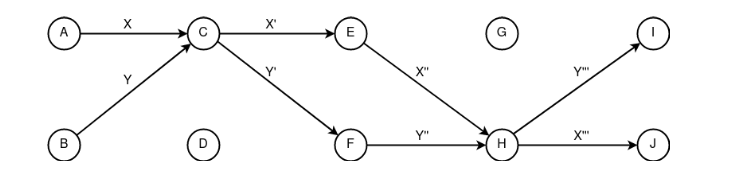
Figure 17. Application of the constructs “following” and “mixing”, where {A, B} are senders of packed information {X, Y}, {I, J} are recipients of information {X''', Y’’’} An example of network communication with sender anonymity based on the constructs “entanglement”, “mixing” and “diffusion”. The safety of the above concept rests on the “mixing” unit» C, which should have the property of “accumulation” and on the nodes {A, B, C}, which must have the property of “periodicity”».

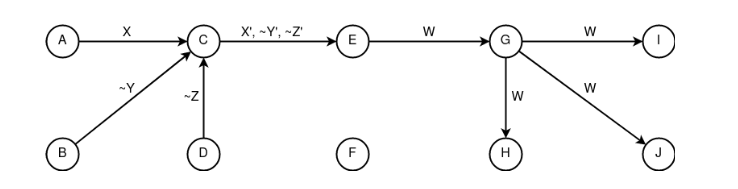
Figure 18. Application of the constructs “mixing”, “entanglement” and “dissemination”, where A is the sender of packed information X, C is the “mixing” node, {E, G, H, I, J} are recipients of unpacked information W An example of network communication with recipient anonymity based on the constructs “following”, “splitting”, “reduction” and “dissemination”. The security of the above concept rests on the “information” node» h, which must have the property of “accumulative».

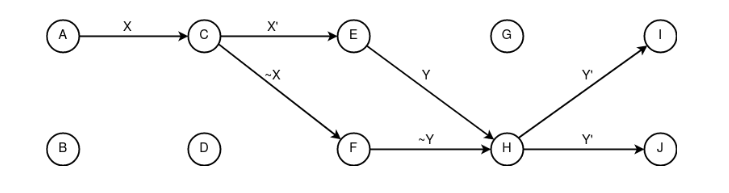
Figure 19. Application of the constructs “following”, “splitting”, “convergence” and “dissemination”, where A is the sender of the packed information X, E is the recipient of information X', C is the “splitting” node, H is the “information” node, Y – generated response An example of network communication with anonymity of the sender and recipient based on the “dissemination” construct. The security of the above concept rests on all network nodes, which must have the property of “periodicity”».

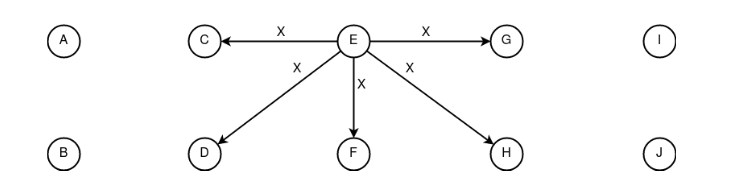
Figure 20. Application of the “dissemination” construct, where the simultaneous formation of information X by subject E occurs in a specific period.
Thus, any anonymous network mechanism is built, firstly, on design primitives (constructs), and secondly, on defined properties. Due to the above compositions, appropriate levels of anonymity, performance and applicability are acquired.
Conclusion
This paper examined network anonymity from the perspective of its primary definition (based on anonymous networks), development (based on the stages of anonymity) and constructs (based on design primitives). For each type of analysis, subsequent structuring of the definition of anonymity becomes possible..
For example, it becomes possible to provide a more detailed description of certain networks that represent, to one degree or another, anonymity.
The Tor network is an anonymous network based on the sixth stage of anonymity, built on the constructs of “following” and “mixing” with the property of “threading”".
The Mixminion network is an anonymous network based on the sixth stage of anonymity, built on the “mixing” construct with the “accumulative” property".
The Herbivore network is an anonymous network based on the first stage of anonymity, built on the construct of "distribution" with the property of "periodicity"".
The Hidden Lake Service network is an anonymous network based on the fifth stage of anonymity, built on the construct of "distribution" with the property of "periodicity"".
Etc.
In addition, the definition of anonymity (from the stage side) can provide an understanding of how anonymous the network is truly. Let's say networks such as Freenet, Retroshare, Bitmessage, Bitcoin are not anonymous, because they do not have any kind of confusing routing, but at the same time they are client-safe applications.